Architecture Weekly Issue #121. Articles, books, and playlists on architecture and related topics. Split by sections, highlighted with complexity: 🤟 means hardcore, 👷♂️ is technically applicable right away, 🍼 - is an introduction to the topic or an overview. Now in telegram and Substack as well.
Highlights
Stop using GraphQL 👷♂️
Like 5 years ago there were tons of hype on GraphQL: blog posts, conference talks, security best practices and many other content. Every second project was making a decision if they need to proceed with GraphQL or REST. Well... it's time to say that GraphQL brings more problem security and performance-wise, than it's solves. Amazingly detailed, long post on why GraphQL is highly probably don't fit you.
#performance #security
Distributed Snapshots: Chandy-Lamport protocol 🤟
Saving a state of a single process is easy. However, if you have a distributed computation across a network, saving a consistent state becomes pretty challenging. I am sharing a description of the Chandy-Lamport paper with formal problem description and the protocol to solve the issue.

#distributedsystems #paper
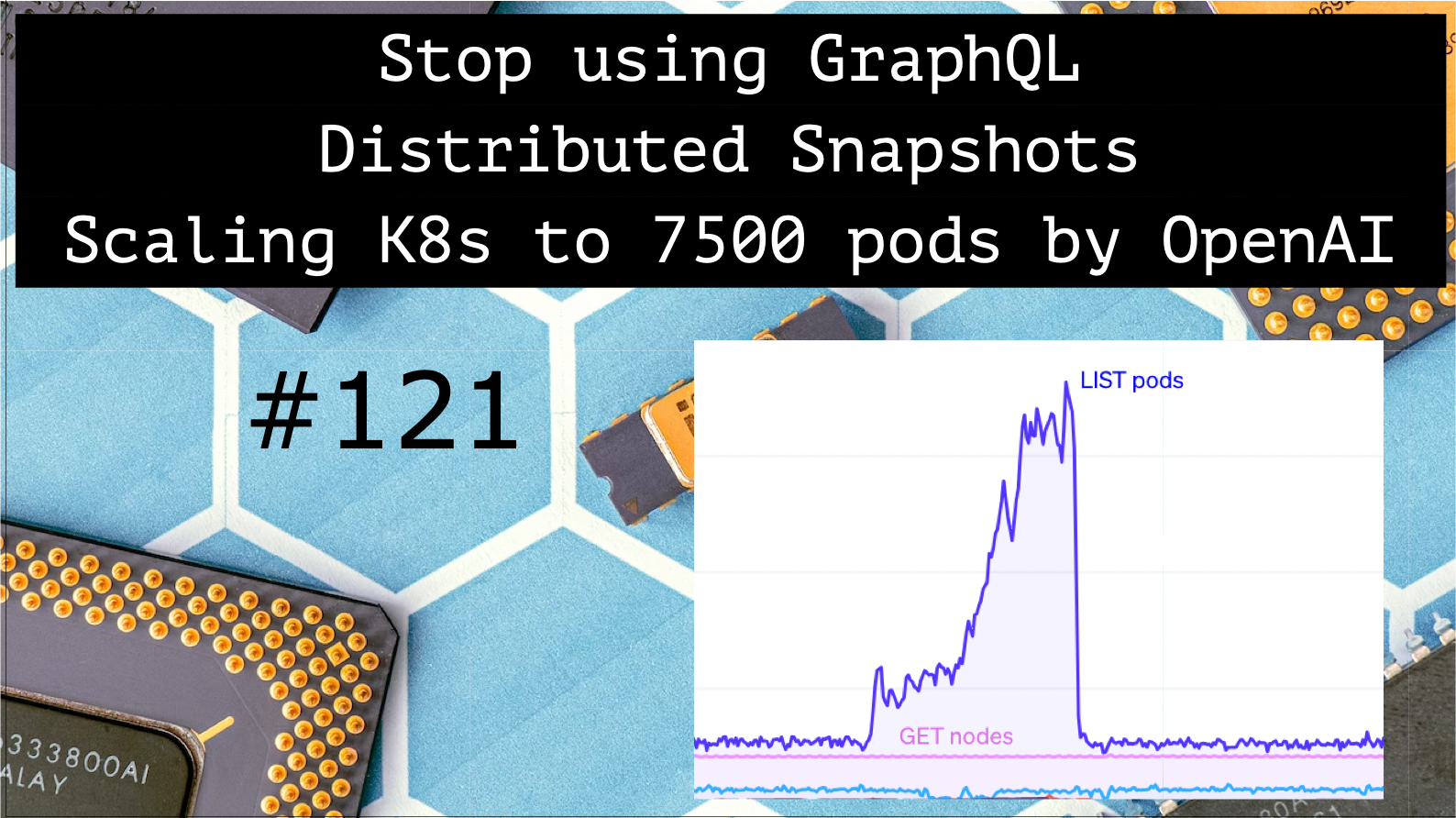
Scaling Kubernetes to 7500 nodes 👷♂️
How many pods do you have in your Kubernetes clusters? OpenAI has 7500. And with new scale coming new challenges like IP Addresses, monitoring, and others. Find this long read from OpenAI for technical details and observability hints.
#observability
Business Oriented System Design Course

If you wanna rock system design interviews, be able to design performant, reliable and secure software architecture, and advance in software engineering career, I have a course to help with this!
Opening up the second cohort of Business Oriented System Design Course. What's included, what the participants of the first cohort think about it and other details - on this page.
Follow-Up
Understanding and verifying security of Diffie-Hellman parameters 🤟
While searching the internet I found an article which claimed that it's impossible to create a common key without exchange in advance. Formally this is not true: Diffie-Hellman algorithm allows you to elaborate a common key in untrusted environment if you verified the identity of your counterpart. However, not every number can be used in this algorithm. Hubert Kario explains how to generate and verify a needed number in this algorithm.

#security
Shitty Code is terrible, innit? 👷♂️
Another piece of my own content :) Programmers always tell you to write clean code. I object: there are situations when shitty code is preferable, and the reason is business, not engineering. Find out an example!

#casestudy
Software Architecture Diagrams with C4 Model 🍼
C4 model is spot on in terms of allocating the responsibility of different diagrams for documenting your solution. Alex Pliutau explains all the 4 levels and spices it up with the diagrams as code examples

#documentation
Geosharded Recommendations 👷♂️
Meeting apps like Tinder make perfect case for geosharding, as people are searching for other people in a radius. The question though is how to organize those shards so there are no hotshards, at least unjustified once? Tinder tech blog covers their considerations for geosharding with Elasticseach

#performance #casestudy
Etsy Tax Calculations 👷♂️
Bolt operates at 45+ countries, and taxes are a huge pain before you even start paying them, because you have to show the rate on the app and reflect it on an invoice. Etsy shows how they do it using 3rd party tax provider in their blog post.
WARNING 🇺🇦
The brutal and unjustified war against Ukraine continues already 2 years. If you want to help Ukraine directly visit this fund.
Big thanks to Nikita, Constantin, Anatoly, Oleksandr, Dima, Pavel B, Pavel, Robert, Roman, Iyri, Andrey, Lidia, Vladimir, August, Roman, Egor, Roman, Evgeniy, Nadia, Daria, Dzmitry, Mikhail, Nikita, Dmytro, Denis and Mikhail for supporting the newsletter. They receive early access to the articles, influence the content and participate in the closed group where we discuss the architecture problems. Join them at Patreon or Boosty!