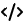Architecture Weekly Issue #128. Articles, books, and playlists on architecture and related topics. Split by sections, highlighted with complexity: 🤟 means hardcore, 👷♂️ is technically applicable right away, 🍼 - is an introduction to the topic or an overview. Now in telegram and Substack as well.
Highlights
Using Redis for real-time RAG goes beyond a Vector Database 👷♂️
LLMs are great, but they can lie to you if they don't have an answer or base the answer on the unreliable sources. Retrieval Augmented Generation is an approach to solve the problem while basically double checking on the LLM yield. Redis used as Vector Database can help with that and improve the generation performance at the same time. See the architecture in the article.

#casestudy #performance #genai
Using S3 as a container registry 👷♂️
ECR is a default container registry in AWS, but if pushing the docker images is time sensitive for you, then you will find out that uploading the same image to S3 is 5 times faster than with S3 in minimum time. Find out the reasons why it happens in the article.

#performance
The past, present and future of local-first 🤟
Martin Kleppmann discusses the development and principles of Local First software, tracing its roots from early CRDT research to current implementations like Automerge. Martin proposes a more precise definition that includes multi-device functionality and robustness against network and server failures. The talk outlines the benefits to both users and developers, suggesting a future direction involving a generic syncing service to standardize protocols and enhance app interoperability.
#video
Follow-Up
Defense-in-Depth: A Layered Strategy for Modern Cybersecurity 🍼
Security tactics include encryption, backups, access controls, DoS protection and many more. The modern software is so complex and hackers are so advanced, you can't merely apply couple of tactics here and there and feel safe. Instead you should be going with holistic approach like Defense-in-Depth where every layer is putting maximum effort into security assuming all the other layers already failed.

#security
Event-driven = Loosely coupled? Not so fast! 🍼
Direct endpoint calls are considered coupled. But coupling can take different forms including semantic, time, topology and many more. Gregor Hohpe depicts those coupling and explains the difference between messages and events.
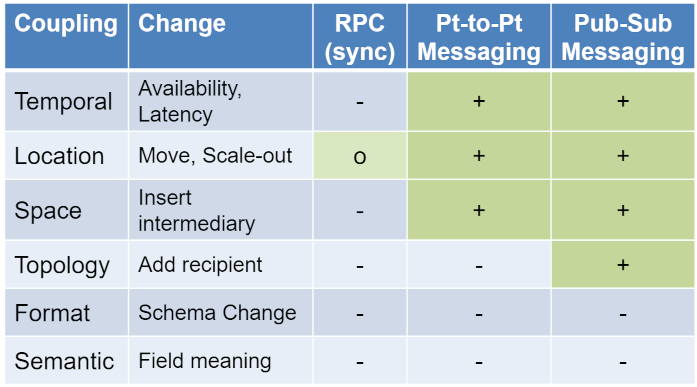
#patterns
TiDB - A Raft-based HTAP Database 🤟
And can't let you go without a paper! Typically you either go with an OLTP DB for operational loads, or augment it with OLAP DB for analytical queries. Another option is to have a single solution working in a hybrid model - HTAP. TiDB is exactly that and it is processing almost all the payload inside Bolt. Find a paper about this peculiar database and how it operates with multiple Raft groups of row and column stores
#db
A beginner’s guide to Phantom Read anomaly 👷♂️
Speaking about the database, I would like to continue sharing the articles about isolations anomalies. This time time it's phantom read - read the data in 1 transaction which is being inserted by another one. Find out how MVCC can prevent it.

Organization Architecture 🍼
Alex Ewerlöf discusses how the software architecture is impacted by the organizational structure in a pretty entertaining way, and how relationships in the organization tree affects system reliability. No practical solutions there, but funny read indeed.

#ea
WARNING 🇺🇦
The brutal and unjustified war against Ukraine continues already 2 years. If you want to help Ukraine directly visit this fund.
Big thanks to Nikita, Constantin, Anatoly, Oleksandr, Dima, Pavel B, Pavel, Robert, Roman, Iyri, Andrey, Lidia, Vladimir, August, Roman, Egor, Roman, Evgeniy, Nadia, Daria, Dzmitry, Mikhail, Nikita, Dmytro, Denis and Mikhail for supporting the newsletter. They receive early access to the articles, influence the content and participate in the closed group where we discuss the architecture problems. Join them at Patreon or Boosty!